Linux is thought for requiring a password to do something to the core system. It’s due to this, many contemplate Linux to be a bit safer than most working methods (although not excellent by any means). Having a powerful password, and an excellent sudoer coverage is nice, but it surely’s not fool-proof, and generally it isn’t sufficient to guard you. That’s why many within the safety discipline have taken to utilizing two-factor authentication on Linux
In this text, we’ll go over the right way to allow two issue authentication on Linux utilizing Google Authenticator.
Set up
Utilizing Google Authenticator is feasible, due to a pam plugin. Use this plugin with GDM (and different desktop managers that help it). Right here’s the right way to set up it in your Linux PC.
Be aware: Earlier than establishing this plugin in your Linux PC, please go to the Google Play Store (or) Apple App Store and obtain Google Authenticator, because it’s a key a part of this tutorial.
Ubuntu
sudo apt set up libpam-google-authenticator
Debian
sudo apt-get set up libpam-google-authenticator
Arch Linux
Arch Linux doesn’t help the pam Google authentication module by default. Customers will as a substitute must seize and compile the module by way of an AUR bundle. Obtain the newest model of the PKGBUILD, or level your favourite AUR helper at it to get it working.
Fedora
sudo dnf set up google-authenticator
OpenSUSE
sudo zypper set up google-authenticator-libpam
Different Linuxes
The supply code for the Linux model of Google Authenticator, in addition to the libpam plugin used on this information is available on Github. If you happen to’re utilizing a non-traditional Linux distribution, head over here and observe the directions on the web page. The directions can assist you compile it from supply.
Set Up Google Authenticator On Linux
A configuration file wants enhancing earlier than pam will work with the Google Authentication plugin. To modify this configuration file, open up a terminal window. Contained in the terminal, run:
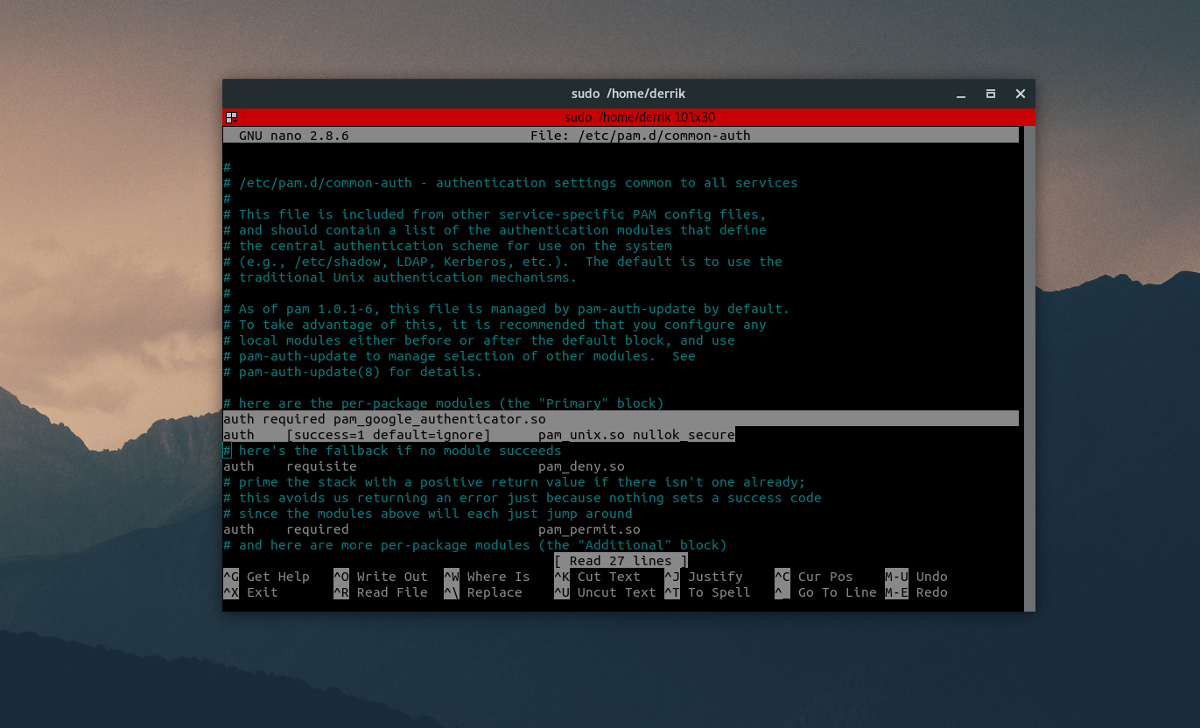
sudo nano /and so on/pam.d/common-auth
Contained in the common-auth file, there’s quite a bit to have a look at. Plenty of feedback, and notes for the way the system ought to use authentication settings between providers on Linux. Ignore all of this within the file, and scroll all the way in which right down to “# here are the per-package modules (the “Primary” block)”. Transfer the cursor under it with the down arrow key, and press enter to make a brand new line. Then write this:
auth required pam_google_authenticator.so
After scripting this new line out, press CTRL + O to save lots of the edit. Then press CTRL + X to exit Nano.
Subsequent, return to the terminal, and kind “google-authenticator”. You’ll then be requested to reply some questions.
The primary query Google Authenticator asks is “Do you want authentication tokens to be time-based”. Reply “yes” by urgent y on the keyboard.
After answering this query, the software will print out a brand new secret key, together with some emergency codes. Write these code down, because it’s essential.
Proceed on and reply the subsequent three query as “yes”, adopted by “no”and “no”.
The final query authenticator asks has to do with fee limiting. This setting when enabled makes it in order that Google Authenticator will solely enable 3 attempt/fail makes an attempt each 30 seconds. For safety causes, we advocate you reply sure to this, but it surely’s completely OK to reply no if fee limiting isn’t one thing you care about.
Configuring Google Authenticator
The Linux facet of issues is working. Now it’s time to configure the Google Authenticator app in order that it really works with the brand new setup. To begin, open the app and choose the choice “enter a provided key”. This brings up an “enter account details” space.
In this space, there are two issues to fill out: the identify of the PC you’re utilizing authenticator with, in addition to the key key you wrote down earlier. Fill each of those out, and Google Authenticator might be operational.
Logging In
You’ve arrange Google Authenticator on Linux, in addition to your cellular gadget and every part works collectively because it ought to. To log in, choose the person in GDM (or LightDM and so on). Instantly after choosing the person, your working system will ask for an authentication code. Open up your cellular gadget, go to Google Authenticator and enter the code that seems into the login supervisor.
If the code is profitable, you’ll then have the ability to enter the person’s passcode.
Be aware: establishing Google Authenticator on Linux doesn’t solely impact the login supervisor. As an alternative, every time a person tries to realize root entry, entry sudo privileges, or do something that requires a password, an authentication code is required.
Conclusion
Having two issue authentication immediately related to the Linux desktop provides an additional layer of safety that needs to be there by default. With this enabled, it’s a lot more durable to realize entry to somebody’s system.
Two issue could be iffy at instances (like when you’re too gradual for the authenticator), however all in all it’s a welcome addition to any Linux desktop supervisor.