Linux has a fame of being pretty safe, and out of the large three working programs it runs into far much less points with regards to privateness. Nonetheless, as safe as Linux might be, there’s all the time room for enchancment. Introducing Firejail. It’s an utility that enables customers to take any working app, and “jail it”, or “sandbox it”. Firejail permits you to isolate an app and forestall it from accessing the rest on the system. The app is the most well-liked program sandboxing software on Linux. It’s due to this, many Linux distributions have determined to ship this software program. Right here’s get the Firejail on Linux.
SPOILER ALERT: Scroll down and watch the video tutorial on the finish of this text.
Set up
Ubuntu
sudo apt set up firejail
Debian
sudo apt-get set up firejail
Arch Linux
sudo pacman -S firejail
Not proud of the repo model of Firejail on Arch? Contemplate constructing the Git version from the AUR as an alternative.
Fedora
Sadly, there isn’t any Firejail bundle for Fedora to be seen. The principle repos don’t have it, and there’s no purpose to imagine it will change. Fedora customers can nonetheless set up the software program, with Copr.
Copr is similar to PPAs on Ubuntu, or the Arch Linux AUR. Any person could make a Copr repo and put software program on it. There are lots of FireJail Copr repos, so if the one we checklist on this article stops updating, be happy to go to the website and discover a substitute.
To get Firejail on Fedora, do:
sudo dnf copr allow ssabchew/firejail sudo dnf set up firejail
OpenSUSE
Like most third-party software program for Suse, customers will discover Firejail within the OBS. Variations of Firejail can shortly be put in for the newest variations of Leap and Tumbleweed. Get them here.
Be sure you click on the 1-click button to put in through YaST.
Different
The supply code for Firejail is available and simple to compile should you’re on an unsupported Linux distribution.
To begin off, set up the Git bundle in your model of Linux. Do that by opening your bundle supervisor, trying to find “git” and putting in it to the system. Be sure you additionally set up any construct instruments particular to your Linux distribution, should you haven’t already (it must be simple to search out, simply test your distro’s wiki). For instance, compiling on Debian/Ubuntu requires build-essential.
As soon as the git bundle has been put in on the system, use it to seize the newest model of the Firejail software program.
git clone
The code is on the system. Enter the downloaded folder to begin the construct course of with the cd command.
cd firejail
Earlier than this software program can compile, you’ll must run a configure. This may scan your PC, and inform the software program what your PC has, what the specs are, and and so forth. That is essential, and with out it, the software program is not going to construct.
configure
This system is configured for compilation. Now, let’s generate a makefile. A makefile has directions for constructing a bit of software program. Do that with the make command.
make
Lastly, set up the firejail software program to your system:
sudo make install-strip
Utilizing Firejail
Sandboxing one thing with Firejail is straightforward. For a fundamental program sandbox, all that’s required is to make use of the “firejail” prefix earlier than getting into a command. For instance: to Sandbox the Gedit textual content editor, and silo if off of the remainder of your Linux set up, you do: firejail gedit within the terminal. That is just about the way it works. For easy sandboxing, that is sufficient. Nonetheless, due to how finicky this software program is, some configuration is required.
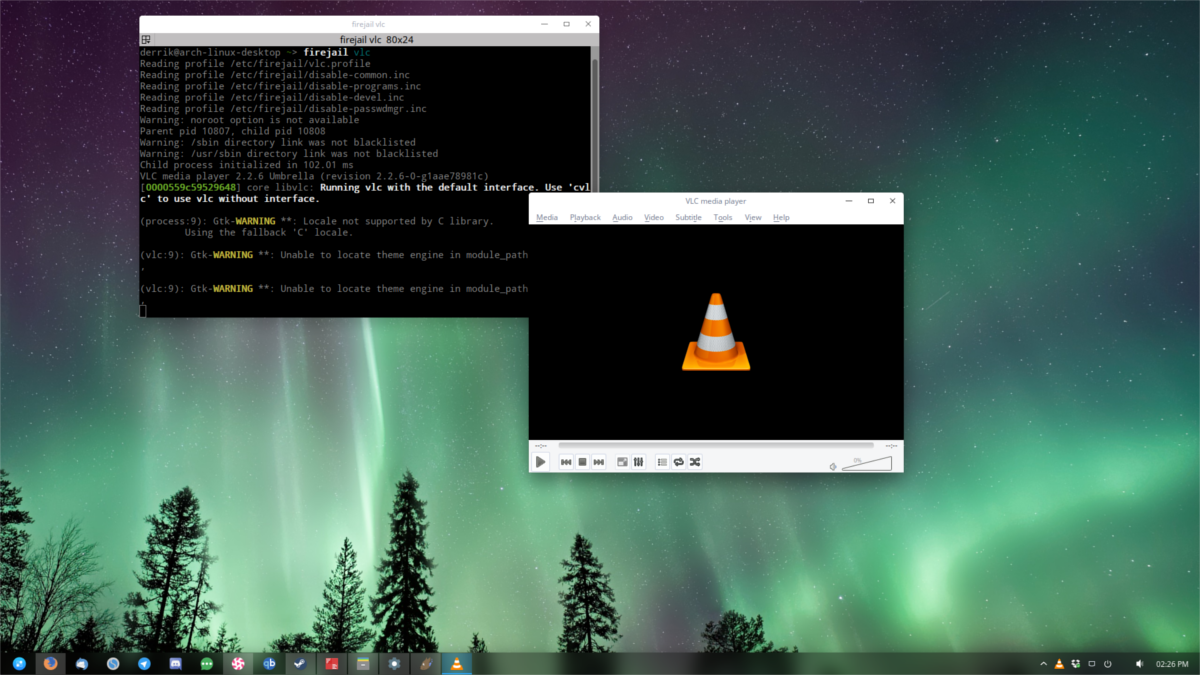
For instance: should you run firejail firefox, the Firefox browser will run in a locked sandbox, and nothing else on the system will be capable to contact it. That is nice for safety. Nonetheless, if you wish to obtain a picture to a listing, chances are you’ll not be capable to, as Firejail could don’t have any entry to each listing in your system and and so forth. Consequently, you’ll must undergo and particularly checklist out the place a sandbox CAN and CANNOT go on the system. Right here’s do it:
Profile Whitelisting And Blacklisting
Blacklisting and whitelisting are a per-app factor. There isn’t any solution to set world defaults for what jailed apps can entry. Firejail has many configuration recordsdata already arrange. They generate sane defaults with these configuration recordsdata, and in consequence fundamental customers received’t must do any enhancing. Nonetheless, should you’re a sophisticated person, enhancing a majority of these recordsdata might be helpful.
Open a terminal, and head over to /and so forth/firejail.
cd /and so forth/firejail
Use the LS command to view all the contents of the listing, and use a pipe to make every web page viewable. Press the enter key to maneuver down the web page.
Discover the configuration file in your app, and preserve word of it. On this, we’ll be persevering with with the Firefox instance.
ls | extra
Open the Firefox firejail profile within the nano textual content editor.
sudo nano /and so forth/firejail/firefox.profile
As acknowledged earlier than, the Firejail app has sane defaults. This implies the builders have gone by way of and arrange defaults that ought to work for many customers. For instance: although the app is jailed, the ~/Downloads listing, and plugin directories on the system can be found. To add extra objects to this whitelist, go to the part of the config file the place every thing is being whitelisted, and write your individual guidelines.
For instance, to make it simpler to add pictures to my Fb profile within the firejail model of Firefox, I’ll want so as to add:
whitelist ~/Footage
The identical premise can be utilized for blacklisting. To stop the sandboxed model of Firefox from seeing particular directories (it doesn’t matter what), be happy to do one thing like:
blacklist ~/secret/file/space
Save your edits with Ctrl + O
Word: “~/” means /house/present person
Conclusion
Sanboxing is an excellent solution to safeguard your self from leaky functions, or dangerous actors trying to steal your knowledge. When you’re paranoid on Linux, it’s in all probability a good suggestion to present this software a severe shot.
